H. Valters
Ethical Penetration tester / DevSecOps / IT Solution Developer / System administrator
Category Archives: Cyber Security
DOM-based open redirection

In this section, we’ll talk about what DOM-based open redirection is, demonstrate how an attack is constructed, and suggest ways to reduce your exposure to DOM-based open-redirection vulnerabilities. What is DOM-based open redirection? DOM-based open-redirection vulnerabilities arise when a script writes attacker-controllable data into a sink that can trigger cross-domain navigation. For example, the following…
DOM-based vulnerabilities
In this section, we will describe what the DOM is, explain how insecure processing of DOM data can introduce vulnerabilities, and suggest how you can prevent DOM-based vulnerabilities on your websites. What is the DOM? The Document Object Model (DOM) is a web browser’s hierarchical representation of the elements on the page. Websites can use…
Examining the database in SQL injection attacks

When exploiting SQL injection vulnerabilities, it is often necessary to gather some information about the database itself. This includes the type and version of the database software and the contents of the database in terms of which tables and columns it contains. Querying the database type and version Different databases provide different ways of querying their version….
Blind SQL injection

In this section, we’ll describe what blind SQL injection is, explain various techniques for finding and exploiting blind SQL injection vulnerabilities. What is blind SQL injection? Blind SQL injection arises when an application is vulnerable to SQL injection, but its HTTP responses do not contain the results of the relevant SQL query or the details…
SQL injection cheat sheet
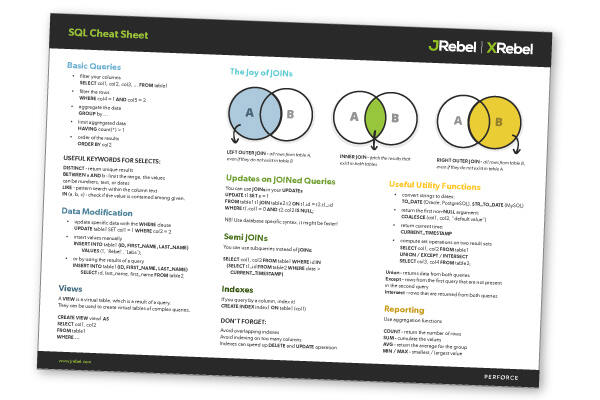
This SQL injection cheat sheet contains examples of the useful syntax that you can use to perform a variety of tasks that often arise when performing SQL injection attacks. String concatenation You can concatenate together multiple strings to make a single string. Oracle ‘foo’||’bar’ Microsoft ‘foo’+’bar’ PostgreSQL ‘foo’||’bar’ MySQL ‘foo’ ‘bar’ [Note the space between the two strings]CONCAT(‘foo’,’bar’)…
SQL injection UNION attacks
When an application is vulnerable to SQL injection and the results of the query are returned within the application’s responses, the UNION keyword can be used to retrieve data from other tables within the database. This results in an SQL injection UNION attack. The UNION keyword lets you execute one or more additional SELECT queries and append the results to the…
SQL injection
In this section, we’ll explain what SQL injection is, describe some common examples, explain how to find and exploit various kinds of SQL injection vulnerabilities, and summarize how to prevent SQL injection. What is SQL injection (SQLi)? SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an…
Cross-site WebSocket hijacking
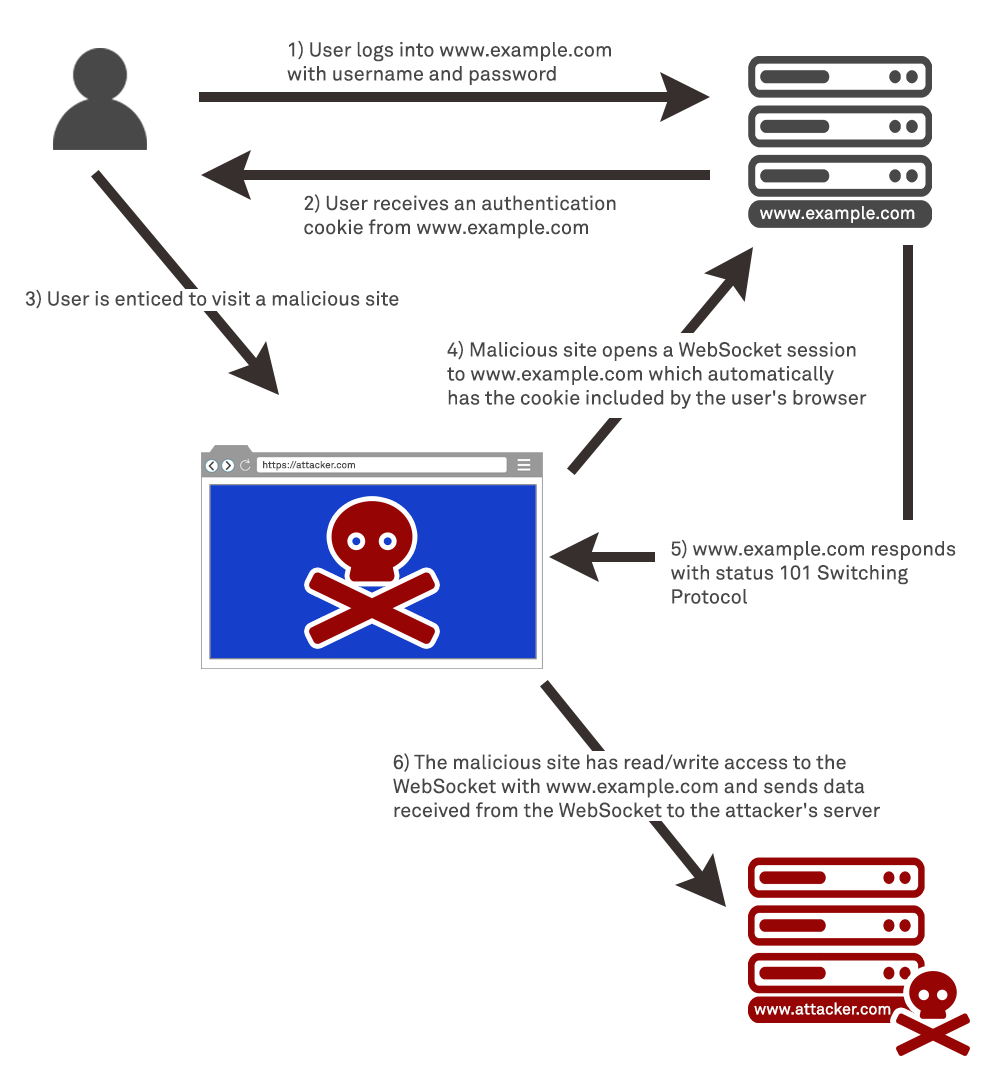
In this section, we’ll explain cross-site WebSocket hijacking (CSWSH), describes the impact of a compromise, and spell out how to perform a cross-site WebSocket hijacking attack. What is cross-site WebSocket hijacking? Cross-site WebSocket hijacking (also known as cross-origin WebSocket hijacking) involves a cross-site request forgery(CSRF) vulnerability on a WebSocket handshake. It arises when the WebSocket handshake request…
What are WebSockets
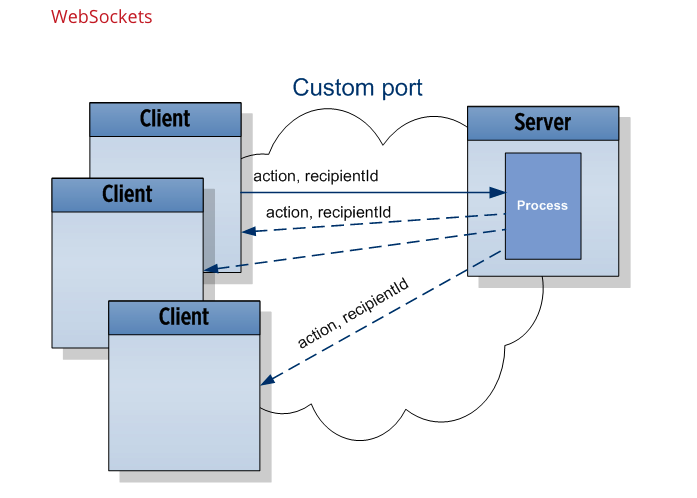
WebSockets is a bi-directional, full-duplex communications protocol initiated over HTTP. They are commonly used in modern web applications for streaming data and other asynchronous traffic. In this section, we’ll explain the difference between HTTP and WebSockets, describe how WebSocket connections are established, and outline what WebSocket messages look like. What is the difference between HTTP and…
Testing for WebSockets security vulnerabilities
In this section, I’l explain how to manipulate WebSocket messages and connections, describe the kinds of security vulnerabilities that can arise with WebSockets, and give some examples of exploiting WebSockets vulnerabilities. WebSockets WebSockets are widely used in modern web applications. They are initiated over HTTP and provide long-lived connections with asynchronous communication in both directions….

