H. Valters
Ethical Penetration tester / DevSecOps / IT Solution Developer / System administrator
Kasm New version v1.15 New VPN function and more
In an age where online threats loom large and privacy concerns are at an all-time high, individuals and organizations alike are seeking robust solutions to safeguard their digital activities. Kasm, a cutting-edge platform, emerges as a potent tool to address these pressing concerns. With its multifaceted features, Kasm offers not only protection for businesses and individuals but also serves as a valuable asset for penetration testers, cybersecurity experts, DevOps, DevSecOps practitioners, system administrators, and office administrators.
Understanding Kasm:
Kasm is a comprehensive solution that provides secure browsing environments through docker. It allows users to access the internet safely, shielded from potential threats such as malware, phishing attacks, and malicious websites. By employing isolated containers for web browsing, Kasm ensures that any harmful activity is contained within the docker container environment, safeguarding users’ devices and networks.
Protection for Businesses and Individuals:
For businesses, Kasm offers a vital layer of defense against cyber threats. By implementing Kasm across their network infrastructure, organizations can mitigate the risk of data breaches and protect sensitive information from falling into the wrong hands. Employees can securely browse the web without fear of compromising corporate networks or inadvertently downloading malware.
Individual users can also benefit from Kasm’s protection, enjoying a secure browsing experience free from tracking, profiling, and intrusive advertisements. Whether conducting online banking transactions, accessing confidential emails, or simply browsing the web for personal interests, Kasm ensures that users remain anonymous and their activities remain private.
Untraceable Online Activities:
One of Kasm’s standout features is its ability to render users virtually untraceable online. By routing web traffic through encrypted channels and employing techniques such as IP address masking and browser fingerprinting prevention, Kasm effectively anonymizes users’ online activities. This capability is particularly valuable for individuals seeking to evade surveillance, censorship, or tracking by malicious actors.
Utilization in Penetration Testing and Cybersecurity:
Penetration testers and cybersecurity experts leverage Kasm as a powerful tool in their arsenal. By simulating various browsing environments within isolated containers, testers can assess the security posture of networks and applications without risking exposure to live threats. Kasm enables testers to conduct reconnaissance, vulnerability scanning, and exploit research in a controlled, safe environment, facilitating more effective assessments and remediation strategies.
Integration in DevOps, DevSecOps, and System Administration:
In the realm of DevOps and DevSecOps, Kasm plays a pivotal role in ensuring the security and integrity of software development pipelines. Developers and system administrators can utilize Kasm to access online resources, documentation, and repositories securely. By isolating browsing activities from development environments, Kasm helps prevent inadvertent exposure to security risks, such as downloading malicious code or accessing compromised websites.
System administrators also benefit from Kasm’s capabilities, using it to securely troubleshoot issues, research solutions, and perform administrative tasks without compromising the stability or security of production systems. By segregating browsing and administration activities from critical infrastructure, administrators can maintain a robust security posture while fulfilling their operational responsibilities.
Protection for Office Administrators:
Office administrators tasked with managing network security and user access can deploy Kasm to enhance their defense mechanisms. By providing employees with secure browsing and working environments, administrators can reduce the likelihood of malware infections, data breaches, and unauthorized access attempts. Kasm empowers administrators to enforce browsing policies, monitor user activity, and mitigate risks effectively, safeguarding the organization’s digital assets and reputation.
Conclusion:
In an era characterized by pervasive online threats and growing concerns over privacy, Kasm emerges as a versatile solution capable of addressing the diverse security needs of individuals and organizations alike. From safeguarding businesses and individuals against cyber threats to empowering penetration testers, cybersecurity experts, DevOps practitioners, and system administrators with enhanced capabilities, Kasm stands at the forefront of cybersecurity innovation. By leveraging its advanced features and robust security measures, users can navigate and work in the digital landscape with confidence, knowing that their online activities are protected, untraceable, and secure.
More use cases and how they can be implemented can be found in my YouTube Video:
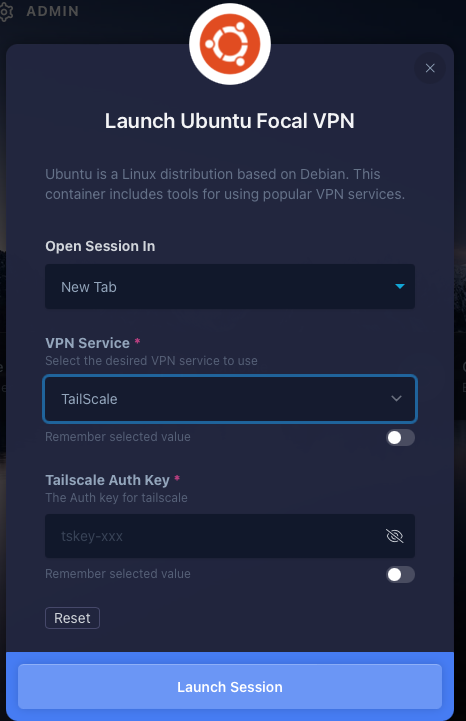
Kasm Ubuntu VPN:
The new feature, that the Kasm team has created with the Ubuntu Docker container you can now have a VPN by using one of the selected VPN options:
OpenVPN
TailScale ( Free for personal use )
WireGuard
Therefore you can Protect your online appearance even more and not only protect online appearance, but also change the locations from where you are browsing the website. With Kasm you already are protected, but this is a double ++ for you in the Online Jungle, where there are a lot of bad actors, malicious websites, and also companies that want to track you for advertisement purposes or creating your digital clone. By clicking here you can see, how it works with TailScale as I tested it in my video.
Overall I find a lot of great use cases for Kasm, as it is a great tool that is easy to implement, easy to use, and can be implemented in any type of IT work. As time goes forward with all the digital treats it gets even harder to determine if the e-mail is a fishing e-mail or the website is safe to browse. Then to protect yourself self Kasm is the way to go. As currently it is free to use and I hope it will stay like that. For companies to protect connections to servers and employees’ browsing also for journalists Kasm is the safe way to go few use cases you can find by clicking here the chapter in my YouTube Video
Kasm Installation:
The installation has been made much faster by the Kasm team. If previously it took some time to do all needed, then now I felt it to finish much quicker than previous. So to Install Kasm, You need a Server or VPS running Ubuntu or Debian. The required resources are
2 CPU Cores
4 GB RAM
50 GB of storage preferably an SSD ( But for better performance, I would recommend an NVMe drive )
Of course, if you have more CPU, RAM, and disk space that is only an advantage on how many things you can run in Kasm at the same time.
The knowledge, that you need to know is on How to access a Linux terminal. So basically you can order a VPS from any VPS hosting provider. Login to the terminal with the SSH connection data, that you received in your e-mail or chose when doing the order. Once you have the VPS ip, root, or user password. Then you need to log into it. On MacOS open a software called terminal. On Windows 11 CMD if you already are using Linux then Just terminal and type:
ssh root@ipAfter executing the above command, it will ask you for the root password, if your hosting provider generates user instead of root, then Just replace root with the hosting provided username, and once you are in the VPS type sudo su to become a root user.
Once you are in the server go to cd /tmp ( to keep your server clean and after reboot the unneeded files are removed )
Always check the Kasm official website which is the latest release, during this article and the YouTube video of the installation, that you can find by clicking here. We have version 1.15 so execute the following command in the terminal ( this will download the 1.15 version )
curl -O https://kasm-static-content.s3.amazonaws.com/kasm_release_1.15.0.06fdc8.tar.gzOnce we have done that, we can now unpack the installer:
tar -xf kasm_release_1.15.0.06fdc8.tar.gzAnd now let’s run the installer:
sudo bash kasm_release/install.shAll the above commands should be executed in your Linux terminal (The VPS that you have logged in ) The Kasm installer will ask you to accept Terms of Service and also if it should create an automatic swap. I suggest you Choose yes and select 16 GB of swap. You can also find the installation with all the Images in my previous written article by clicking here https://www.valters.eu/kasm-workspace-secure-way-of-working-and-digital-it-lab/ as nothing has changed in that part except the version ( so please be aware of the version that you are installing, so that it is the latest ). The YouTube instalaltion guide can be found by clicking here
So maybe by reading this article and or watching my YouTube video. You now have a question will I use the Kasm solution?
The answer is simple. As I browse a lot of tutorials, and a lot of websites and also like to got to the Deep Dark Web. Then yes I consider full-time usage of Kasm. Why? As I want to protect my identity and also my personal data. So when renting a VPS in some countries, then the websites don’t see my IP address instead they see the VPS address and therefore the traceability is gone.
Also, by browsing the Deep Dark Web you need to be careful as one wrong step and your device might get infected, so for protection, I will use Kasm as I would like to keep my files and all the information in my device to my self, not to someone who would like to sell it back to me or something. So In one simple sentence, yes I find many Kasm apps daily usable and needed to protect my online appearance, my data, and my devices. Hopefully, the Kasm team will develop one day an Android and IoS app, so that you can have your Work Place ready at any time when you start your morning, you Open your Kasm in an App start working or check what you need to check, and after that move to your Ipad or Laptop, depending what you want to do.
So I hope you liked this article if you haven’t watched my YouTube video, then I suggest to watch it also don’t be a stranger but become a Subscriber on YouTube or a Follower on Twitter.
YouTube: https://www.youtube.com/@valters_eu
Twitter: https://twitter.com/valters_eu
Kasm: https://kasmweb.com
Thank you.

