H. Valters
Ethical Penetration tester / DevSecOps / IT Solution Developer / System administrator
Category Archives: Web Security
TeamPass a Self-hosted Password manager to increase organization’s CyberSecurity

In today’s digital age, securing sensitive information within organizations is paramount. With cyber threats becoming increasingly sophisticated, the need for robust password management solutions has never been more critical. TeamPass, a web-based password management system, offers an effective solution to this challenge. This article explores the importance of password security, the benefits of implementing TeamPass…
How to Lock down xmlrpc.php in WordPress
This article explains how you can lockdown xmlrpc.php using .htaccess. The WordPress xmlrpc.php endpoint can be misused as an endpoint for brute force attacks. If you do not use xmlrpc.php for any integrations, you might as well disable it completely. Adding these lines to your .htaccess file will disallow access to the endpoint for everyone. Edit your public/.htaccess file and add Note: xmlrpc.php is required by some plugins,…
What is XMLRPC for WordPress and How You Can Stop Hackers From Using It

Website security is a tough thing to solve in the right way. Specifically with security issues related to XML-RPC – as commonly exploited in attacks on WordPress sites. There’s a lot of information available on the internet providing all kinds of solutions, but which are correct? In this article will explain the how, the solutions out there,…
Why Installing a Security Plugin to WordPress Actually Hurt Your Site

WordPress users often lean onto plugins for any required feature or functionality without thinking much about their impact on the site’s performance. There are several WordPress security plugins out there that promise to secure your website from XMLRPC related security issues but in reality, they hurt your site more. Here are some of the reasons…
WordPress Cross-Site Port Attack (XSPA
Cross-site Port Attacks (XSPA) are very common in which the hacker injects the malicious script to retrieve information on TCP ports and IP addresses. In the case of WordPress, XMLRPC is used along with its pingback mechanism to bypass any IP masking such as basic WAF like Cloudflare. In an XSPA attack, the hacker uses pingback….
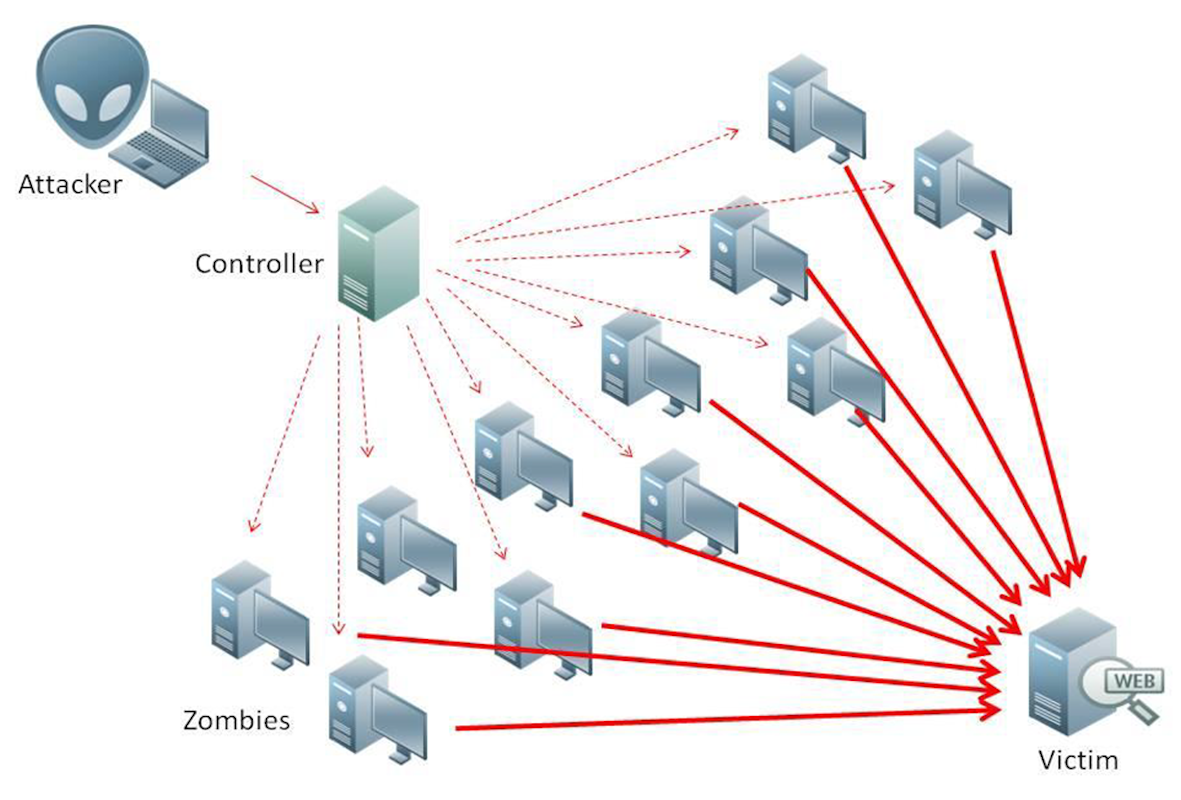
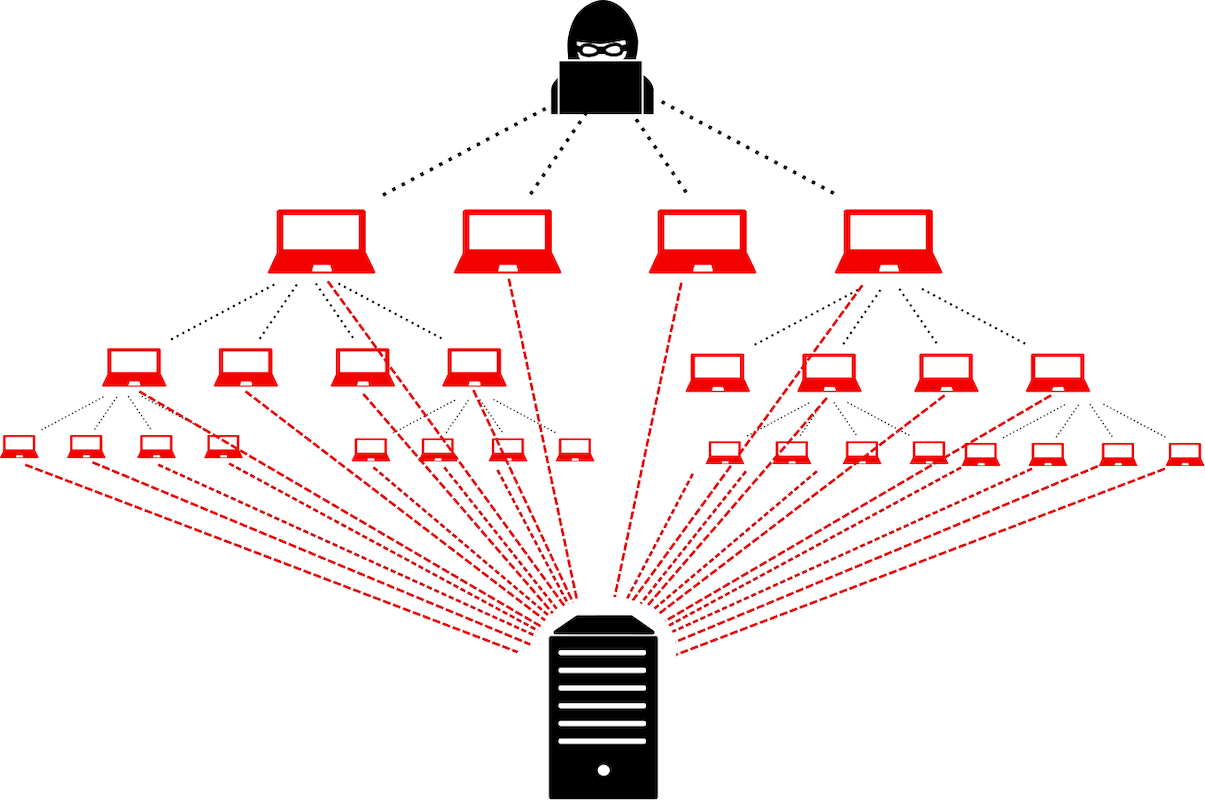
WordPress DDoS Attack

Distributed Denial of Service (DDoS) is one of the most lethal cyber-attacks that can paralyze the server by hitting it with hundreds and thousands of concurrent requests. Hackers use the pingback feature of WordPress along with the xmlrpc.php file to execute such attacks. Ideally, the hacker targets the endpoint or a page that can be…
WordPress Bruteforce Attack

In the Bruteforce attack, the hacker tries to guess the correct username and password by running numerous login attempts. Unfortunately, a large number of WordPress sites use weak admin passwords or do not have any security layer added to stop attackers. Those sites are easily compromised with this type of attack. Others use a strong…
Cross-site scripting

In this section, we’ll explain what cross-site scripting is, describe the different varieties of cross-site scripting vulnerabilities, and spell out how to find and prevent cross-site scripting. What is cross-site scripting (XSS)? Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with…
AngularJS sandbox

In this section, we’ll describe the AngularJS sandbox, explain how exploits can escape from the sandbox, and spell out how content security policy (CSP) can be bypassed in the context of the AngularJS sandbox. What is the AngularJS sandbox? The AngularJS sandbox is a mechanism that prevents access to potentially dangerous objects, such as window or document, in AngularJS template…
How to prevent XSS

In this section, we’ll describe some general principles for preventing cross-site scripting vulnerabilities and ways of using various common technologies for protecting against XSS attacks. Cross-site scripting prevention can generally be achieved via two layers of defense: Encode data on output Validate input on arrival Encode data on output Encoding should be applied directly before user-controllable data is written…

