H. Valters
Ethical Penetration tester / DevSecOps / IT Solution Developer / System administrator
Category Archives: DOM-based
Web-message manipulation

In this section, we’ll explain what web-message manipulation vulnerabilities are and suggest ways to reduce your exposure to them. What is DOM-based web-message manipulation? Web-message vulnerabilities arise when a script sends attacker-controllable data as a web message to another document within the browser. An attacker may be able to use the web-message data as a source by…
DOM-based link manipulation

In this section, we’ll talk about what DOM-based link manipulation is, look at the impact of an attack, and suggest ways of preventing them. What is DOM-based link manipulation? DOM-based link-manipulation vulnerabilities arise when a script writes attacker-controllable data to a navigation target within the current page, such as a clickable link or the submission…
DOM-based WebSocket-URL poisoning

In this section, we’ll talk about how WebSocket URLs can be poisoned using DOM-based attacks, discuss the impact of WebSocket-URL poisoning, and suggest ways you can reduce your exposure to this kind of attack. What is DOM-based WebSocket-URL poisoning? WebSocket-URL poisoning occurs when a script uses controllable data as the target URL of a WebSocket…
DOM-based document-domain manipulation

In this section, we’ll describe DOM-based manipulation of the document.domain property and suggest ways to reduce your exposure to this kind of attack. What is DOM-based document-domain manipulation? Document-domain manipulation vulnerabilities arise when a script uses attacker-controllable data to set the document.domain property. An attacker may be able to use the vulnerability to construct a URL that, if visited…
DOM-based JavaScript injection

In this section, we’ll talk about DOM-based JavaScript-injection vulnerabilities, discuss how they can impact the victim and suggest ways to reduce your exposure to JavaScript-injection vulnerabilities. What is DOM-based JavaScript injection? DOM-based JavaScript injection vulnerabilities arise when a script executes attacker-controllable data as JavaScript. An attacker may be able to use the vulnerability to construct…
DOM-based open redirection

In this section, we’ll talk about what DOM-based open redirection is, demonstrate how an attack is constructed, and suggest ways to reduce your exposure to DOM-based open-redirection vulnerabilities. What is DOM-based open redirection? DOM-based open-redirection vulnerabilities arise when a script writes attacker-controllable data into a sink that can trigger cross-domain navigation. For example, the following…
DOM-based vulnerabilities
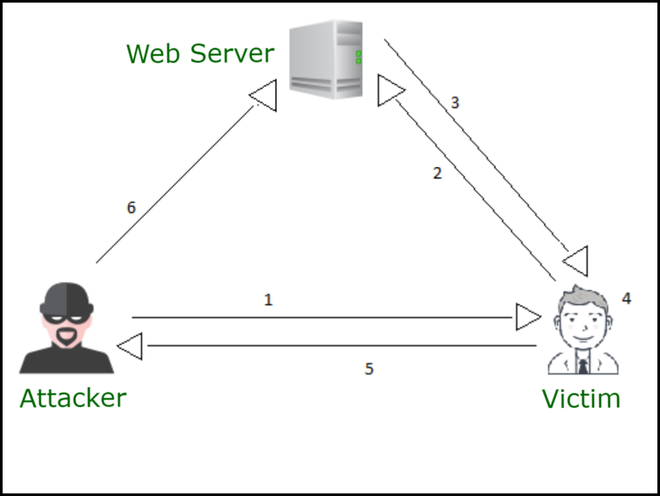
In this section, we will describe what the DOM is, explain how insecure processing of DOM data can introduce vulnerabilities, and suggest how you can prevent DOM-based vulnerabilities on your websites. What is the DOM? The Document Object Model (DOM) is a web browser’s hierarchical representation of the elements on the page. Websites can use…

